Learn how to set up networking for your applications, including VPCs, DNS, VPN, SSH, service discovery, service mesh, and more.
7.1 Public Networking
7.1.1 Public IP Addresses
7.1.2 Domain Name System (DNS)
7.1.3 Example: Register and Configure a Domain Name in Amazon Route 53
Register a domain name
Deploy EC2 instances
Configure DNS records
7.2 Private Networking
7.2.1 Physical Private Networks
Only authorized devices may connect to the private network
The private network uses private IP address ranges
The private network defines connectivity rules
Most devices in a private network access the public Internet through a gateway
7.2.2 Virtual Private Networks
Virtual networks in the cloud
Virtual networks in orchestration tools
Example: Create a VPC in AWS
7.3 Accessing Private Networks
7.3.1 Castle-and-Moat Model
7.3.2 Zero-Trust Model
7.3.3 SSH
How to use SSH
Example: SSH bastion host in AWS
7.3.4 RDP
How to use RDP
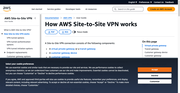
7.3.5 VPN
How to use VPN
7.4 Service Communication in Private Networks
7.4.1 Service Discovery
Service discovery tools
Service discovery tool comparison
7.4.2 Service Communication Protocol
Common protocols
Key factors to consider
7.4.3 Service Mesh
7.4.4 Example: Istio Service Mesh with Kubernetes Microservices
7.5 Conclusion